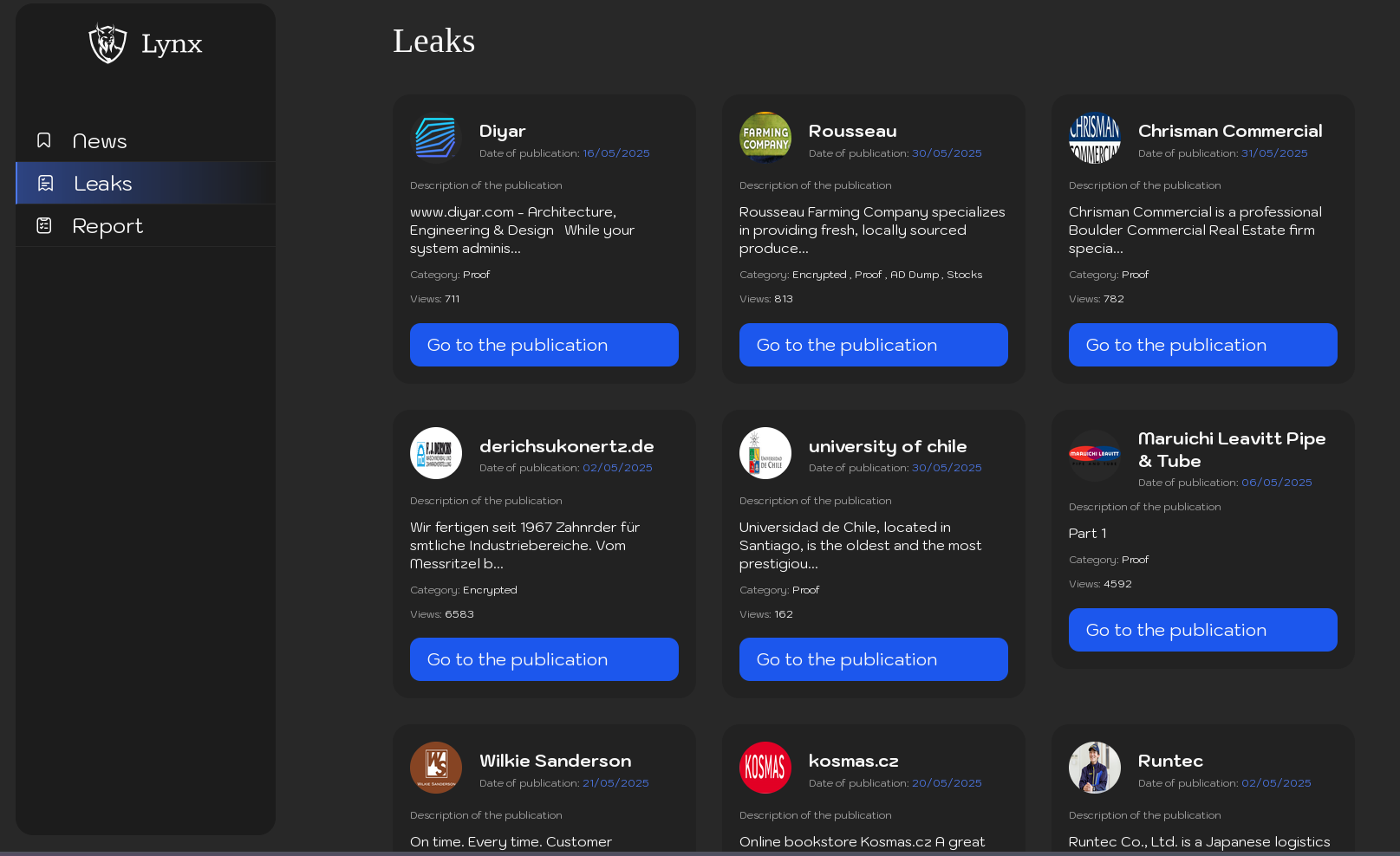
Kairos

| Rules Guidelines for Responding to Data Exfiltration and Extortion Demands Understanding the Situation Data Exfiltration and Investigation: We have conducted a thorough investigation of your network and downloaded all confidential, private, proprietary, legal, financial, and compromising information belonging to you, your customers, and employees, including databases and all valuable documents. This action highlights the insecurity of your infrastructure. Demand for Payment: We are demanding payment in exchange for the secure deletion of the exfiltrated data and to prevent its public exposure. Steps to Restore Normal Operations and Protect Your Data Initiating Negotiations: Contact us using the contact details left in the notes inside your network. In your initial message, include the name of your domain and the names of three random servers from your network to verify your identity as a company representative. Proof of Exfiltrated Data: We will provide you with a list of the exfiltrated files. You can select 5 files from the list that do not contain critical information, and we will send them to you as proof. Payment Details: Payment must be made in Bitcoin. We will provide a cryptocurrency wallet for the payment.You can use a crypto broker or exchange service to purchase the cryptocurrency. Post-Payment Obligations: Within 24 hours of receiving the payment, we will start the process of deleting the exfiltrated data. If you need any specific assurances or additional actions, inform us before making the payment.We will provide a log of the data deletion and a security report with recommendations. Consequences of Non-Payment: You have 7 days to agree on the payment terms. If no agreement is reached within 7 days, we will publish the fact of the data compromise on our website.If the situation remains unresolved after 7 days, we will notify your partners, competitors, and customers and then publish your data in full. This could lead to legal actions, termination of contracts, reputational damage, stock value drops, and potential closure of your organization. Price Formation and Discounts Price Determination: The price is determined based on your organization’s income, expenses, documents, and reports. The price is non-negotiable. 20% discount is available if payment is made within 5 days of the initial request. Recommendations Avoid External Involvement: We advise against contacting law enforcement or recovery companies, as this could lead to data disclosure, legal issues, and reputational damage. Do not inform anyone about the incident to avoid rumors and information leaks. Negotiate directly and involve your IT department for any technical support needed. Name: Rules Preview text: Guidelines for Responding to Data Exfiltration and Extortion Demands Understanding the Situation Data Exfiltration and Investigation: We have conducted a thorough investigation of your network and downloaded all confidential, private, proprietary, legal, financial, and compromising information belonging to you, your customers, and employees, including databases and all valuable documents. This action highlights the insecurity of your infrastructure. Demand for Payment: We are demanding payment in exchange for the secure deletion of the exfiltrated data and to prevent its public exposure. Steps to Restore Normal Operations and Protect Your Data Initiating Negotiations: Contact us using the contact details left in the notes inside your network. In your initial message, include the name of your domain and the names of three random servers from your network to verify your identity as a company representative. Proof of Exfiltrated Data: We will provide you with a list of the exfiltrated files. You can select 5 files from the list that do not contain critical information, and we will send them to you as proof. Payment Details: Payment must be made in Bitcoin. We will provide a cryptocurrency wallet for the payment.You can use a crypto broker or exchange service to purchase the cryptocurrency. Post-Payment Obligations: Within 24 hours of receiving the payment, we will start the process of deleting the exfiltrated data. If you need any specific assurances or additional actions, inform us before making the payment.We will provide a log of the data deletion and a security report with recommendations. Consequences of Non-Payment: You have 7 days to agree on the payment terms. If no agreement is reached within 7 days, we will publish the fact of the data compromise on our website.If the situation remains unresolved after 7 days, we will notify your partners, competitors, and customers and then publish your data in full. This could lead to legal actions, termination of contracts, reputational damage, stock value drops, and potential closure of your organization. Price Formation and Discounts Price Determination: The price is determined based on your organization’s income, expenses, documents, and reports. The price is non-negotiable. 20% discount is available if payment is made within 5 days of the initial request. Recommendations Avoid External Involvement: We advise against contacting law enforcement or recovery companies, as this could lead to data disclosure, legal issues, and reputational damage. Do not inform anyone about the incident to avoid rumors and information leaks. Negotiate directly and involve your IT department for any technical support needed. |
| post | date |
|---|---|
Jericho Fire Department | 03/06/2025 |
Neighborhood Development Services | 21/05/2025 |
Durham Arts Council | 20/05/2025 |
Looper Goodwine | 13/05/2025 |
Colorado Pulmonary Intensivists | 24/04/2025 |
The Derby High School | 23/04/2025 |
d-line | 17/04/2025 |
RFMS, Inc. | 08/04/2025 |
Galesburg Area Chamber of Commerce | 07/04/2025 |
State's Attorney Office | 01/04/2025 |
Fred Salvucci | 10/03/2025 |
USA Rice<br /> | 05/03/2025 |
Vitenas Cosmetic Surgery | 03/03/2025 |
Fireplace Warehouse | 24/02/2025 |
Dane Court Grammar School | 17/02/2025 |
Toi Toi USA | 17/02/2025 |
Medical Reports | 04/02/2025 |
Casper's Truck Equipment | 04/02/2025 |
DEL Packaging | 29/01/2025 |
The Urswick School | 20/01/2025 |
Nightingale Hammerson | 17/01/2025 |
Real Tax | 16/01/2025 |
Combined Pool and Spa | 15/01/2025 |
J.G. Electrical Installations | 15/01/2025 |
Austin's Financial Solutions | 19/12/2024 |
Eisenhower Carlson | 16/12/2024 |
Anetic Aid | 13/12/2024 |
Tri County Property Management | 13/12/2024 |
Archdiocese of Louisville | 13/12/2024 |
T & M Equipment | 06/12/2024 |
Brown Packing | 28/11/2024 |
Tacoma Engineers | 26/11/2024 |
The Physical Medicine and Rehabilitation Center | 18/11/2024 |
Formosa Certified Public Accountants | 18/11/2024 |
Clay Platte Family Medicine Clinic | 18/11/2024 |
Accounting & Advisory Services, | 18/11/2024 |
Sunshine Center | 18/11/2024 |
Kansas Regenerative medicine centre | 18/11/2024 |